Starting Feb. 27, you'll be asked to complete an extra step when using the Microsoft Authenticator app with Azure Multi-Factor Authentication (MFA). Microsoft is launching this update to comply with new MFA guidelines
from the U.S. Cybersecurity Agency that protect your account against hackers.
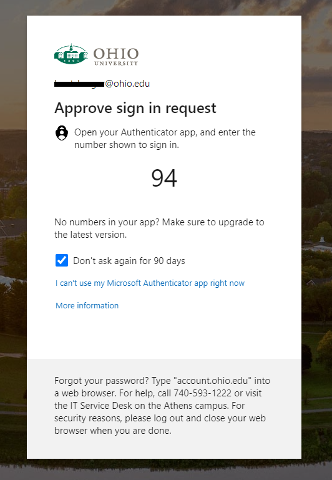
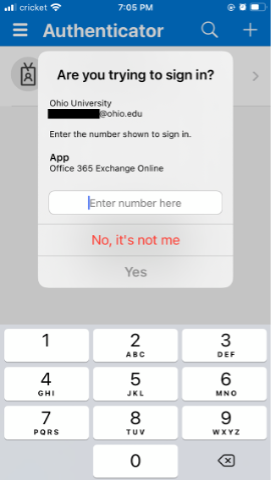
After Feb. 27, the next time you're prompted to authenticate, you'll see a number on your device’s screen. Then, you'll enter that number on your phone's Microsoft Authenticator app to authenticate.
Authenticating this way prevents a new form of hacking called MFA fatigue attacks. These attacks are growing in popularity and Microsoft recorded 40,000 in a single month. Several prominent companies, like Uber , were also recently hacked this way. In an MFA fatigue attack, a hacker steals your password in a phishing attempt and sends repeated MFA push notifications to your phone, hoping you'll accidentally approve them (and let the hacker access your data!). Number matching protects you from accidentally accepting an authentication request that you didn't initiate.
This update only applies to the Microsoft Authenticator app on your smartphone. If you use a phone call or text message (SMS) to authenticate, this update does not impact you. No action is required - Microsoft is applying this update to all accounts by default on Feb. 27.
For a quicker authentication experience, you can:
- Select Remember me for 90 days at any OHIO log-in screen
- Disable app lock so you can open the Microsoft Authenticator app without entering your phone’s passcode.
The Office of Information Technology (OIT) is here to help with any questions about this update. View Using the Microsoft Authenticator App with Azure MFA for more information or visit help.ohio.edu, where you can submit a ticket or contact the IT Service Desk.